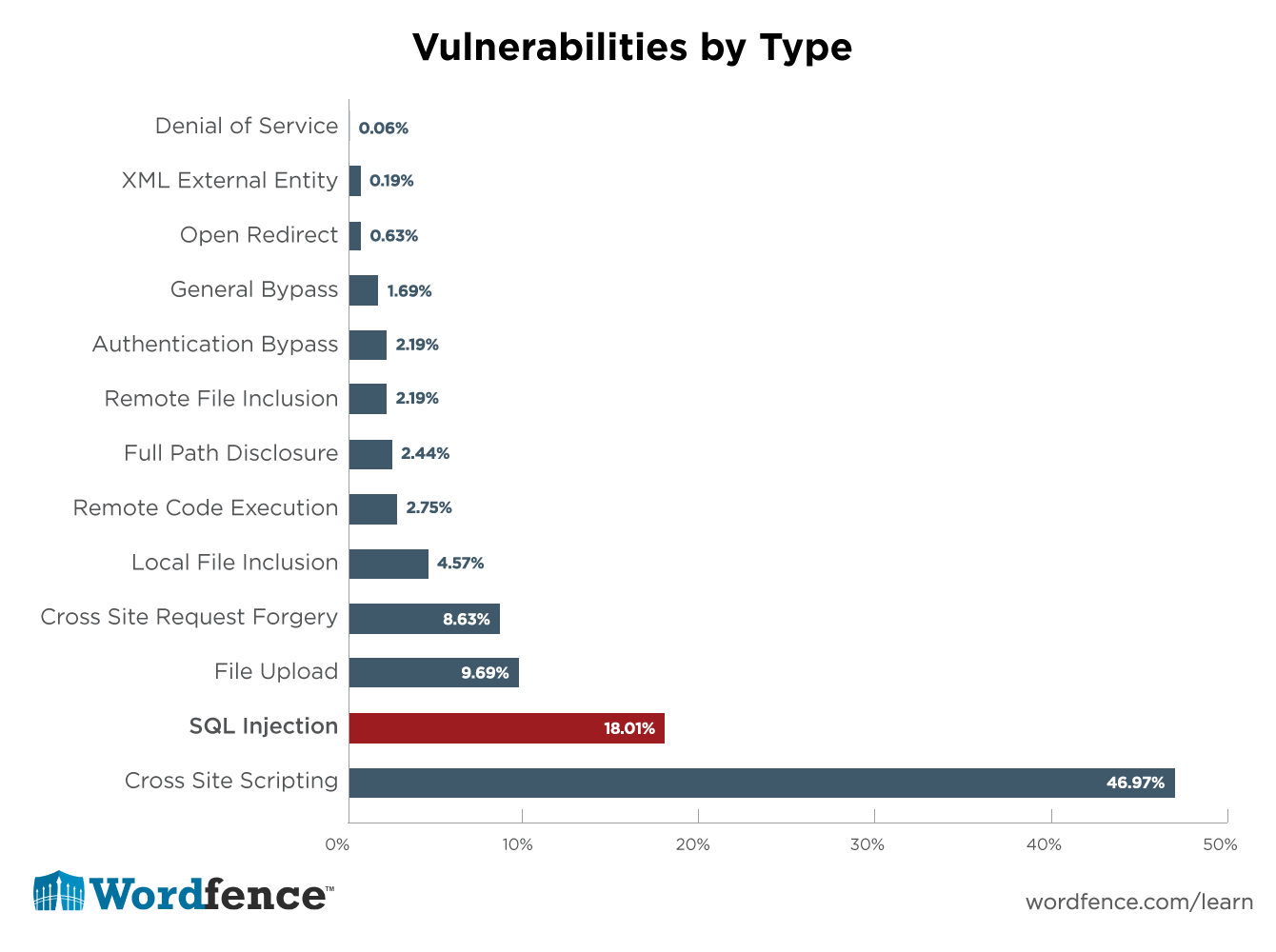
Types Of Sql Injection
Immortalized by 'Little Bobby Drop Tables' in, SQL injection (SQLi) was first discovered in 1998, yet continues to plague web applications across the internet. Even the lists injection as the number one threat to web application security. Learn why. Get the latest from CSO. What is SQL injection?SQL injection is a type of attack that can give an adversary complete control over your web application database by inserting arbitrary SQL code into a database query.The good news?

SQL injection is the lowest of the low-hanging fruit for both attackers and defenders. SQLi isn't some cutting edge NSA Shadow Brokers kit, it's so simple. This is script kiddie stuff—and fixing your web application to mitigate the risk of SQLi is so easy that failure to do so looks more and more like gross negligence. Types of SQL injection attacksThere are several types of SQL injection, but they all involve an attacker inserting arbitrary SQL into a web application database query.
The simplest form of SQL injection is through user input. Web applications typically accept user input through a form, and the front end passes the user input to the back-end database for processing. If the web application fails to sanitize user input, an attacker can inject SQL of their choosing into the back-end database and delete, copy, or modify the contents of the database.An attacker can also modify cookies to poison a web application's database query.
Cookies store client state information locally, and web applications commonly load cookies and process that information. A malicious user, or, can modify cookies to inject SQL into the back-end database.Server variables such as HTTP headers can also be used as a SQL injection attack vector.
Forged headers containing arbitrary SQL can inject that code into the database if the web application fails to sanitize those inputs as well.Second-order SQL injection attacks are the sneakiest of the bunch, because they aren't designed to run immediately, but much later. A developer who correctly sanitizes all their input against an immediate attack may still be vulnerable to a second-order SQLi when the poisoned data is used in a different context. How to test for SQL injection vulnerabilitiesSQL injection, as a technique, is older than many of the human attackers using SQLi today.
SQLi attacks are rudimentary and have long since been automated. Tools like SQLninja, SQLmap, and Havij make it easy to test your own web applications, but also make it easy for attackers.Ten years ago, a rampaged across the internet. Cut to the present: Not much has changed. Despite a widespread awareness of SQL injection as a problem, a large percentage of web applications remains vulnerable.Automated testing tools can keep you a step ahead of attackers looking for an easy payday. Pentesting your web applications with a tool like SQLmap is a quick way to see if your mitigations are adequate. SQLmap supports pretty much every major database in use today and can detect and exploit most known SQL injection vulnerabilities.Sanitize your input, but test to verify your mitigations are successful.
A useful reminder: are two sides to the same coin. SQL injection exampleLet's look at a basic SQL injection attack. Suppose you've built a web application that lets customers enter their customer IDs and retrieve their customer profiles. The web application front end passes the user-entered customer ID to the back-end database.
Data is one of the most vital components of information systems. Database powered web applications are used by the organization to get data from customers.is the acronym for Structured Query Language. It is used to retrieve and manipulate data in the database.What is a SQL Injection?SQL Injection is an attack that poisons dynamic SQL statements to comment out certain parts of the statement or appending a condition that will always be true. It takes advantage of the design flaws in poorly designed web applications to exploit SQL statements to execute malicious SQL code.In this tutorial, you will learn SQL Injection techniques and how you can protect web applications from such attacks.How SQL Injection WorksThe types of attacks that can be performed using SQL injection vary depending on the type of database engine. The attack works on dynamic SQL statements.
Types Of Sql Injections
A dynamic statement is a statement that is generated at run time using parameters password from a web form or URI query string.Let’s consider a simple web application with a login form. Gender wikipedia. The code for the HTML form is shown below.
FROM users WHERE email = $POST'email' AND password = md5($POST'password');HERE,.The above statement uses the values of the $POST array directly without sanitizing them.The password is encrypted using MD5 algorithm.We will illustrate SQL injection attack using sqlfiddle. Open the URL in your web browser. You will get the following window.Note: you will have to write the SQL statementsStep 1) Enter this code in left paneCREATE TABLE `users` (`id` INT NOT NULL AUTOINCREMENT,`email` VARCHAR(45) NULL,`password` VARCHAR(45) NULL,PRIMARY KEY (`id`));insert into users (email,password) values (' This email address is being protected from spambots.
You need JavaScript enabled to view it.' ,md5('abc'));Step 2) Click Build SchemaStep 3) Enter this code in right paneselect. from users;Step 4) Click Run SQL. You will see the following result.
Suppose user supplies This email address is being protected from spambots. You need JavaScript enabled to view it. And 1234 as the password.
The statement to be executed against the database would beSELECT. FROM users WHERE email = ' This email address is being protected from spambots. You need JavaScript enabled to view it.' AND password = md5('1234');The above code can be exploited by commenting out the password part and appending a condition that will always be true.
Let’s suppose an attacker provides the following input in the email address field.This email address is being protected from spambots. You need JavaScript enabled to view it.' OR 1 = 1 LIMIT 1 - ' xxx for the password.The generated dynamic statement will be as follows.SELECT.
FROM users WHERE email = ' This email address is being protected from spambots. You need JavaScript enabled to view it.'
OR 1 = 1 LIMIT 1 - ' AND password = md5('1234');HERE,. This email address is being protected from spambots. You need JavaScript enabled to view it. Ends with a single quote which completes the string quote.OR 1 = 1 LIMIT 1 is a condition that will always be true and limits the returned results to only one record.- ' AND is a SQL comment that eliminates the password part.Copy the above SQL statement and paste it in SQL FiddleRun SQL Text box as shown belowHacking Activity: SQL Inject a Web ApplicationWe have a simple web application at that is vulnerable to SQL Injection attacks for demonstration purposes only. The HTML form code above is taken from the login page. The application provides basic security such as sanitizing the email field. This means our above code cannot be used to bypass the login.To get round that, we can instead exploit the password field.
Various Types Of Sql Injection
The diagram below shows the steps that you must followLet’s suppose an attacker provides the following input.Step 1: Enter This email address is being protected from spambots. You need JavaScript enabled to view it. As the email address.Step 2: Enter xxx') OR 1 = 1 -.Click on Submit button.You will be directed to the dashboardThe generated SQL statement will be as followsSELECT.
FROM users WHERE email = ' This email address is being protected from spambots. You need JavaScript enabled to view it.' AND password = md5('xxx') OR 1 = 1 - ');The diagram below illustrates the statement has been generated.HERE,.The statement intelligently assumes md5 encryption is used.Completes the single quote and closing bracket.Appends a condition to the statement that will always be trueIn general, a successful SQL Injection attack attempts a number of different techniques such as the ones demonstrated above to carry out a successful attack.Other SQL Injection attack typesSQL Injections can do more harm than just by passing the login algorithms. Some of the attacks include.Deleting data.Updating data.Inserting data.Executing commands on the server that can download and install malicious programs such as Trojans.Exporting valuable data such as credit card details, email, and passwords to the attacker’s remote server.Getting user login details etcThe above list is not exhaustive; it just gives you an idea of what SQL InjectionAutomation Tools for SQL InjectionIn the above example, we used manual attack techniques based on our vast knowledge of SQL. There are automated tools that can help you perform the attacks more efficiently and within the shortest possible time.
These tools include.SQLSmack -.SQLPing 2 -.SQLMap -How to Prevent against SQL Injection AttacksAn organization can adopt the following policy to protect itself against SQL Injection attacks. User input should never be trusted - It must always be sanitized before it is used in dynamic SQL statements. Stored procedures – these can encapsulate the SQL statements and treat all input as parameters. Prepared statements –prepared statements to work by creating the SQL statement first then treating all submitted user data as parameters. This has no effect on the syntax of the SQL statement. Regular expressions –these can be used to detect potential harmful code and remove it before executing the SQL statements. Database connection user access rights –only necessary access rights should be given to accounts used to connect to the database.
This can help reduce what the SQL statements can perform on the server. Error messages –these should not reveal sensitive information and where exactly an error occurred. Simple custom error messages such as “Sorry, we are experiencing technical errors.
The technical team has been contacted. Please try again later” can be used instead of display the SQL statements that caused the error.Hacking Activity: Use Havij for SQL InjectionIn this practical scenario, we are going to use Havij Advanced SQL Injection program to scan a website for vulnerabilities.Note: your anti-virus program may flag it due to its nature. You should add it to the exclusions list or pause your anti-virus software.The image below shows the main window for Havij.